The day after the last U.S. soldier had departed Afghanistan, President Joe Biden contended, “We will maintain the fight against terrorism in Afghanistan and other countries. We just don’t need to fight a ground war to do it.”1 Specifically, the Biden administration has touted the use of “over-the-horizon capabilities” to remotely surveil and carry out operations against terrorist operatives and targets without a permanent U.S. military presence on the ground.2 This approach is logical. Strategic documents produced by both the Trump and Biden administrations have emphasized interstate competition with Russia and China, implying that fewer resources should be dedicated to counter-terrorism efforts.3 Biden’s announcement marking the end of the U.S. military presence in Afghanistan indeed highlighted that “there’s nothing China or Russia would rather have, would want more in this competition than the United States to be bogged down another decade in Afghanistan.”4
Coupled with disillusionment with large-scale counter-insurgency campaigns designed to stabilize fragile states, America’s emphasis on strategic competition likely portends a durable turn to less resource-intensive approaches to combating transnational terrorist groups.5 Targeted killing will likely be the primary tool that the United States employs. Though not always wielded from over the horizon, this instrument has been particularly attractive to the United States since 9/11. Prior to the May 2011 raid on Osama bin Laden’s compound, the United States had managed to kill scores of al-Qaeda senior and mid-level leaders and specialists in Pakistan’s restive northwest frontier through the use of drones.6 Targeted killing has not just been a component of the U.S. war against al-Qaeda’s Pakistan-based leadership. The United States has used this tactic in its campaigns against al-Qaeda’s affiliates across South Asia, the Middle East, and Africa, as well as against the Islamic State.7 Nor is the United States the only country to target the leadership of terrorist or insurgent groups. Israel has relied extensively on the targeted killing of mid-level and senior members of Palestinian terrorist groups and Lebanese Hizballah; Rhodesian security forces targeted foreign-based Zimbabwe African National Union and Zimbabwe African People’s Union insurgent leadership; and covert Spanish forces carried out targeted killings of Basque separatist leaders in France.8
Yet, lethal targeting’s contribution to counter-terrorism campaigns remains under debate. Some find that it often imposes considerable costs on the targeted groups, while others argue that it offers more drawbacks than benefits.9 This disagreement has been particularly apparent in commentary and scholarship related to the drone campaign in Pakistan. Although none have claimed that drone strikes would be sufficient to strategically defeat al-Qaeda, U.S. policymakers have often asserted that drone strikes degraded al-Qaeda’s personnel roster, reduced its organizational efficiency and control, and led it to consider abandoning its safe haven in the Federally Administered Tribal Areas (FATA) of Pakistan.10 Studies supporting the effectiveness of this campaign have maintained that these outcomes are the mechanisms linking statistical correlations between successful strikes and violence trends in the FATA or between drone strikes and qualitative changes in the organizational strength of the targeted groups.11 Other accounts have downplayed drone strikes’ ability to meaningfully affect terrorist groups’ human resources, organizational efficiency and control, and safe havens, and have often argued that strikes can be counterproductive.12
These disagreements over the effectiveness of the drone campaign in Pakistan matter not just because they revolve around the use of force against one of the more consequential terrorist groups of the 21st century, but also because of the campaign’s broader relevance to the future of U.S. counter-terrorism efforts. If lethal targeting can yield immediate and apparent success, it would suggest that the United States might be able to inflict damage on or contain transnational terrorist groups while keeping opportunity costs tolerable. A null or counterproductive effect would suggest just the opposite and could call into question the reliability of lethal targeting writ large.
Through a comprehensive evaluation of declassified internal correspondence between al-Qaeda leaders recovered in bin Laden’s Abbottabad compound, this study aims to provide a direct assessment of the effects of U.S. drone strikes on al-Qaeda’s organizational capabilities and performance. That is, the study asks: Did the drone campaign render al-Qaeda unable to replace personnel killed in the campaign with equally skilled operatives, undermine its organizational efficiency or internal control, and reduce its reliance on its safe haven in Pakistan’s tribal regions, as many policymakers claim and theories of its effectiveness imply? If so, when in the campaign did these effects become apparent?
This study uncovers novel evidence that U.S. drone strikes did have an appreciable effect on many of these dimensions of al-Qaeda’s organizational capabilities. This challenges a bevy of theories and claims regarding the ineffectiveness of high-value targeting and precision airpower in general and the U.S. drone campaign in Pakistan in particular. It also finds, however, that these results were less pronounced than some of the more sanguine assessments might expect and that they emerged quite late in the drone campaign. Targeted killing should thus not be thought of as a necessarily expedient or flawless option for pacifying or disrupting the ability of terrorist groups to plot and execute attacks.
The remainder of this paper proceeds as follows. It begins by reviewing the literature and commentary on precision airpower, targeted killing, and the U.S. drone campaign, deriving three sets of divergent claims about the effectiveness of drone strikes. It then reviews the present study’s research design, before investigating the veracity of these competing predictions through the use of new primary-source documents. It concludes with a discussion of the implications of this study for scholarship and policy.
Debating the Drones
U.S. drone strikes in Pakistan have been the topic of much policymaker commentary and scholarly attention, yet there is little unanimity as to their effectiveness. In this section, I outline predictions and claims made by optimistic and pessimistic schools of thought on the drone campaign’s impact on al-Qaeda. The section is organized around contradictory prognoses regarding the effects of drone strikes on al-Qaeda’s personnel quality, organizational efficiency and control, and safe-haven viability.
Personnel Quality
Sustaining terrorist campaigns requires skilled personnel to forge documents, build bombs, lead operatives in the field, and assist in the “flow of information, resources, skills, and strategic direction between the top and the bottom of the organization.”13 The available pool of individuals who are both willing to join a terrorist group like al-Qaeda and have these important skillsets will naturally be limited. There are disagreements regarding whether drone strikes have been truly able to drain al-Qaeda’s pool of talented cadres.
Many have found that personnel turnover caused by lethal targeting can force a terrorist group to promote less-qualified replacements.14 Among the most common claims made by proponents of drone strikes has thus been that they have degraded the quality of al-Qaeda’s human capital, rendering the group unable to promote replacements or, alternatively, forcing it to promote unqualified personnel into more senior roles.15 In his 2009 testimony before the U.S. Senate Select Committee on Intelligence, for example, Director of National Intelligence Dennis Blair reported that leadership losses had “made it more difficult for al-Qa’ida to identify replacements, and in some cases the group has had to promote more junior figures considerably less skilled and respected than the individuals they are replacing.”16 This line of reasoning has similarly been present in academic studies. Patrick Johnston and Anoop Sarbahi, for example, attribute decreases in violence after the killing of “high value” individuals to the loss of those individuals’ “valuable skills, resources, or connections.”17
Targeted killing should thus not be thought of as a necessarily expedient or flawless option for pacifying or disrupting the ability of terrorist groups to plot and execute attacks.
Others have argued that terrorist groups with bureaucratic structures and procedures will have little problem generating deep pools of specialized personnel and talented leaders who can be promoted once a senior leader or middle manager is killed.18 Al-Qaeda’s well-documented standard operating procedures and specialized organizational roles could thus insulate the group from the costs of personnel turnover.19 Jenna Jordan, for example, finds little evidence that drone strikes degraded al-Qaeda, claiming that “organizations with bureaucratic institutions [like al-Qaeda] should have an easier time” replacing leaders.20
Organizational Efficiency and Control
Leaders of terrorist organizations face the challenge of balancing internal efficiency — the amount of time and resources needed to perform organizational tasks — and control — the ability to monitor and otherwise maintain the responsiveness and loyalty of subordinate members — with the need to remain concealed from external surveillance.21 This tradeoff exists because the activities that these leaders carry out to manage organizational processes and maintain the loyalty and responsiveness of their subordinates produce detectible intelligence signatures, in turn putting these leaders in the crosshairs of states conducting counter-terrorist efforts.22 Avoiding counter-terrorist surveillance thus requires carrying out fewer of these activities, in theory leading to less efficient, responsive, and cohesive organizations.
Although scholars do not necessarily dispute this fundamental organizational tradeoff, they do disagree as to whether al-Qaeda was able to overcome it when facing the drone campaign. One perspective holds that intensive lethal targeting campaigns cause terrorist leaders to go into hiding or adopt more restrictive communications protocols, slowing organizational processes and undermining leaders’ ability to control the behavior and maintain the loyalty of subordinates.23 Many have thus argued that drone strikes inhibited al-Qaeda leadership’s ability to efficiently and effectively manage the group’s internal affairs. In a speech at the National Defense University outlining his administration’s counter-terrorism strategy, President Barack Obama contended in 2010, for example, that al-Qaeda’s “remaining operatives spend more time thinking about their own safety than plotting against us.”24 Daniel Byman similarly argues that drone strikes could limit al-Qaeda’s ability to manage its relationships with its affiliates in Iraq, North Africa, and Yemen.25 Decreases in leader availability and communications can also undermine organizational cohesion. Drawing on extensive field research, Asfandyar Mir finds that reductions in senior leader activity undermined al-Qaeda’s organizational trajectory, to include its ability to retain personnel.26
Others have argued that terrorist groups can adopt organizational procedures and decision-making models that allow them to overcome the tradeoffs between organizational security, efficiency, and control.27 More specifically, terrorist groups can institute decentralized decision-making processes that delegate greater authority further down the chain of command to trusted subordinates, requiring less direct supervision and monitoring from senior leaders for the organization to function.28 Under these conditions, periods of reduced management activity need not derail the speed of a terrorist group’s processes or the responsiveness of its operatives, as well-screened and highly committed subordinates can proceed without senior-level direction.
A number of studies have, in turn, described al-Qaeda’s Pakistan-based organization as being comprised of a centralized decision-making apparatus at senior levels that provides strategic and operational guidance to “strong-willed” and ideologically committed subordinate commanders and affiliates who are given a considerable amount of latitude to execute operations.29 It is often implicitly or explicitly argued that this would render al-Qaeda’s efficiency and control resilient, even when its leaders need to adopt a lower profile and offer less direct supervision. Drawing on an empirical analysis of plots against the West, Paul Cruickshank contends, for example, that al-Qaeda’s decentralized structure allowed it to continue plotting and attempting to execute attacks on the West during the drone campaign.30
Safe-Haven Viability
Just as sustaining a terrorist campaign requires skilled personnel and functioning organizational processes, it often also requires safe havens. By safe havens, I refer to physical territory from which groups can plot attacks, train and deploy cadres abroad, and house senior leaders and their families.31 Whereas policymakers have often asserted that drone strikes might lead al-Qaeda to abandon its safe haven in Pakistan — the FATA — theories of coercive airpower and observed local opposition to drone strikes dispute this claim.
Several analyses suggest drone strikes could erode al-Qaeda’s safe haven. As CIA director Michael Hayden noted in 2008, “By making a safe haven feel less safe, we keep al-Qaeda guessing.”32 CIA director Leon Panetta echoed this assessment in 2009, claiming, “Serious pressures have been brought to bear on al-Qaida’s leaders in Pakistan’s tribal areas … . One measure of our success is that al-Qaida is seeking shelter elsewhere.”33 Mir comes closest to evaluating this directly, tracing how the Tehrik-e-Taliban Pakistan and al-Qaeda began to relocate and close some of their “organizational bases” within the FATA due to the drone campaign.34
Two lines of analysis would make predictions that conflict with findings and claims discussed above. First, scholarship on coercive airpower has generally found that airstrikes only deny territory to opposing forces when conducted in support of capable and motivated ground units.35 Because the drone campaign in Pakistan was not a component of any combined-arms approach to gaining territorial control in the FATA, this theory would predict that precision strikes would have been unlikely to lead the group to abandon its stronghold. Moreover, although commentators and scholars who find drone strikes to be ineffective do not necessarily make direct claims regarding how they might have affected the strength of al-Qaeda’s safe haven in the FATA, several have argued that drone strikes might have served to alienate local populations from the United States.36 This so-called “blowback effect” could have rendered local Pashtun communities more likely to house or otherwise support militant groups like al-Qaeda, at the very least nullifying any insecurity the group might have felt after a successful strike.37
Summary
Policymakers and scholars offer several competing claims regarding the ability of drone strikes to degrade the quality of al-Qaeda’s talent pool, reduce its efficiency and control, and erode its safety in the FATA. Because it would require reliable and honest inside accounts from senior al-Qaeda leaders, direct evidence in support of these claims has been fleeting. In the section that follows, I outline my approach to evaluating these predictions, which involves drawing on the vast collection of documents captured in the raid on bin Laden’s Abbottabad compound, a repository that offers novel insight into the organizational processes and decision-making of al-Qaeda’s senior leadership and one that has not yet been comprehensively reviewed to address this important topic.
Research Design
This study evaluates hypotheses related to the effect of drone strikes on the quality of al-Qaeda’s personnel, its organizational efficiency and control, and the viability of its safe haven in the FATA. To provide the best chance of observing these empirical relationships directly, it draws on internal correspondence between al-Qaeda leaders. The use of archival evidence raises the issue not only of the biases and drawbacks of the sources themselves, but of how documentary evidence was sampled and how it will be weighed to make causal claims.38 The next two sections address these issues in turn.
Source Material
This study uses Arabic-language correspondence between al-Qaeda operatives from the files captured in the May 2011 raid on bin Laden’s compound. A portion of the original Arabic documents, as well as English translations, were declassified in several waves, first through the Combatting Terrorism Center at the West Point Academy in 2012, and then through three separate releases made available via the Office of the Director of National Intelligence. On Nov. 17, 2017, the CIA made the remaining 470,000 recovered files available to the public through what I refer to in this study as the Abbottabad Compound Collection.39
Like many archival collections, the Abbottabad Compound Collection is vast, disorganized, and not immediately searchable. It consists of tens of thousands of Arabic-language documents ranging from one to hundreds of pages, without any guide as to each document’s significance. Among this collection are religious works, educational materials for children, software manuals, and other miscellany that are of little utility for addressing the topic of this study. Because reading all of the material in this collection was not feasible, I draw on only a sample of the documents for this study.
Just as sustaining a terrorist campaign requires skilled personnel and functioning organizational processes, it often also requires safe havens.
Any sampling strategy creates the prospect of bias. If my approach were more likely to create a corpus of documents reflecting either al-Qaeda’s resilience or its vulnerability, it would naturally call into question the study’s findings.40 To guard against this, I culled the thousands of documents in several steps. First, I drew on those documents already released by the Combatting Terrorism Center and the Office of the Director of National Intelligence to gain an initial baseline of the modal length, formatting, and key Arabic words used in al-Qaeda correspondence. I then created a broader, searchable archive of the entire collection of the over 25,000 Word, PDF, and Excel documents released by the CIA. I searched this larger set of documents using al-Qaeda leaders’ names and kunyas (nicknames), as well as several other key terms, ranging from the very general (e.g., message, martyrdom, Waziristan) to the very specific (e.g., drones, bombings, targeting, security precautions), that would likely be used in official al-Qaeda correspondence. As my collection of relevant al-Qaeda documents grew, I created new search terms and included more names of al-Qaeda leaders before repeating the process. Although these searches often yielded documents of varying lengths, no documents that were relevant to this study exceeded 100 pages. I then sorted the full document collection by document length and scanned through all of those that were 100 pages or less to gather any that were missed in the key word searches. In the process, I gathered additional key words to again search in the full, unfiltered collection.
In total, the collection I used for this study consists of over 400 Arabic-language documents. The content of these documents varies. Just over 250 of them were correspondences to, from, or between senior al-Qaeda leaders. These deal with a range of topics, including personnel promotions, the behavior of affiliates, and external operations. The collection also includes around 100 documents that are routine correspondence between al-Qaeda family members. The remaining documents are a mix of draft statements, budgets, manuals, and longer-form reports commissioned or written by al-Qaeda’s upper echelons.
This 400-document collection provides unparalleled insight into the internal machinations of a highly clandestine organization, but still has important limitations that I have tried to remedy wherever possible. First, written communications could reflect the personal biases, idiosyncrasies, or misperceptions of their authors, some of whom may have strategic incentives to misrepresent information they are passing to their leaders.41 To address this concern, I draw on multiple pieces of correspondence involving different al-Qaeda leaders for my empirical observations, when available, while also noting whether and how individual senior leaders’ assessments and behavior changed over time as the drone campaign proceeded.
Next, the Abbottabad Compound Collection can only offer systematic information on the upper echelons of al-Qaeda’s Pakistan-based leadership prior to May 2011. As such, I cannot conclude from these documents that al-Qaeda’s affiliates or associates were similarly robust or otherwise vulnerable to drone strikes. I also cannot rule out the possibility that correspondence occurring at lower levels of the organization, through other means, or after May 2011 might conflict with these assessments.
Finally, although the documents released by the CIA in late 2017 only excluded those that were protected by copyright, as well as pornography, duplicate files, and files whose release “would directly damage efforts to keep the nation secure,” the documents may have been censored or deleted by the terrorist group itself.42 Even a cursory examination of the documents captured in Abbottabad, however, strongly suggests that bin Laden failed to censor or delete sensitive documents, even when asked to do so. The documents refer to many issues that the group likely never intended to be public, including its dealings with the Islamic Republic of Iran, the movement of bin Laden’s family members, and preparations for external operations targeting the West.43 The collection also includes messages and topics that were explicitly marked as “very secret” or where the sender instructed the reader to destroy the message upon reading it.44
Ultimately, the Abbottabad collection provides an authoritative, but still incomplete and likely flawed, archival source. I made every effort to minimize these flaws through a multi-tiered sampling approach, using multiple sources of correspondence for my observations, and exploiting temporal variance in individual al-Qaeda operatives’ assessments for causal leverage. Where possible, I also draw on complementary evidence from other sources, to include recent secondary works tracing al-Qaeda’s post-9/11 history. I turn next to my approach to using this evidence to measure my outcome variables in the section that follows.
Measuring Outcomes
This study evaluates the relationship between drone strikes and al-Qaeda’s quality of personnel, organizational efficiency and control, and safe-haven viability. Each of these outcomes has observable indicators that should manifest themselves in al-Qaeda’s internal correspondence. Table 1 summarizes these indicators.
| VARIABLE | INDICATORS |
|---|---|
| Personnel Quality | Execution of planned succession |
| Reservations about replacements' qualifications | |
| General concerns with available bench of leaders, skilled personnel, or other specialists | |
| Organizational Efficiency and Control | Reduction in frequency of meetings, movement of personnel, or communications |
| Defections, insubordination, or opportunism by middle- and lower-tier operatives or affiliated groups | |
| Safe-Haven Viability | Redirection of incoming personnel |
| Partial or complete evacuation | |
| Perceived changes in local support |
Table 1: Variables and Indicators
I code any changes in the depth of al-Qaeda’s pool of qualified personnel using several criteria. First, I assess al-Qaeda succession plans executed after the loss of operational and strategic leaders. If al-Qaeda failed to nominate a replacement for an individual killed in a drone strike, it would suggest that its human capital may have been depleted. Second, when nominees are put forward, I trace any reservations that al-Qaeda operatives express about that individual’s qualifications or subsequent performance in the position. Beyond the context of succession or the competence of specific replacements, I also weigh any general concerns that al-Qaeda senior leaders express regarding the availability or capability of its bench of leaders, skilled personnel, or other specialists.
The second set of outcomes that I examine relate to al-Qaeda’s organizational efficiency and senior leaders’ control over subordinates. To assess whether drone strikes affected these dimensions of al-Qaeda’s organizational performance, I take into account any recommended and institutionalized reductions in the frequency of meetings, movement of personnel or resources, or communications. I then assess whether there were any subsequent delays in decision-making or slowing of organizational procedures. With respect to internal control, I seek evidence of any dissension within al-Qaeda’s ranks — whether in the form of defections, insubordination, or an increase in opportunistic behavior by al-Qaeda members — that follows or coincides with reductions in senior leader availability.
Finally, I consider a number of observable activities by al-Qaeda to be indicative of a change in the group’s reliance on the FATA. The first of these is the redirection of any incoming personnel from the tribal areas to other regions, either within Pakistan or further afield. Second is any effort to permanently relocate select personnel, families, or operational components and activities from the FATA, or any authorizations and concrete steps toward a complete evacuation from the region. Third, and more broadly, is any post-strike changes in local support for al-Qaeda, whether in the form of providing sanctuary, funding, materiel, or new recruits.
When al-Qaeda leaders make opposite reflections or decisions, I surmise that drone strikes failed to degrade this dimension of al-Qaeda’s organizational capabilities or behavior.45 Where reflections related to these variables are altogether absent from al-Qaeda’s correspondence, I assume that this dimension of al-Qaeda’s organizational capability, performance, or perception was unaffected by drone strikes.46
If al-Qaeda failed to nominate a replacement for an individual killed in a drone strike, it would suggest that its human capital may have been depleted.
The goal of this analysis is to attribute these outcomes to drone strikes, rather than other concurrent and potentially confounding counter-terrorism instruments. I rely on two types of inferential approaches to do so. First, I seek direct, “smoking-gun” evidence wherein al-Qaeda explicitly attributes shortages of skilled personnel, a slowing of organizational procedures, inability to exert command and control over its components or personnel, or a reduction in the viability of its FATA safe haven to drone strikes.47 Of course, smoking-gun evidence is rare in archival research, and its absence may not necessarily disprove a hypothesis.48 I also identify evidence that fulfills a “hoop test,” wherein al-Qaeda mentions these challenges, but does not directly attribute them to drone strikes.49 Where I employ this type of evidence, I provide context to plausibly rule out alternative causes and highlight any uncertainty I have regarding the role of drone strikes in producing those effects.
Empirical Analysis
This section evaluates the extent to which drone strikes degraded the quality of al-Qaeda’s human resources, organizational processes, and safe haven. It begins with an overview of al-Qaeda’s presence and activities in Pakistan’s tribal areas and temporal patterns in U.S. drone strikes. It then evaluates how these strikes influenced al-Qaeda’s organizational behavior and capabilities in turn.
Al-Qaeda Central and U.S. Drone Strikes in Pakistan’s Northwest Frontier
In the wake of the 9/11 attacks and the subsequent fall of the Taliban’s Islamic Emirate, al-Qaeda’s leaders and their families dispersed.50 Some senior operatives, not to mention members of bin Laden’s family, fled to Iran, where they were first offered limited sanctuary but were eventually arrested by Iranian authorities.51 Other al-Qaeda operatives moved into Pakistan’s urban centers, including Karachi, Lahore, and Rawalpindi, where they continued to plot attacks against Western targets.52 Al-Qaeda’s operational activities in Pakistan’s cities drew notice from Pakistani and U.S. authorities, and a number of subsequent arrests led al-Qaeda to flee to Pakistan’s tribal areas.53
From its safe haven in Pakistan’s tribal regions, al-Qaeda’s senior leaders carried out a number of activities. Al-Qaeda directly supported operations in Afghanistan, Pakistan, and the West. Afghanistan and Pakistan operations appeared to consume the lion’s share of al-Qaeda’s budget, according to the group’s financial manager and senior lieutenant Sheikh Saeed, who reported to bin Laden in early 2010 that “the bulk of our budget –approximately 80% -is spent on work inside Afghanistan and Pakistan.”54 Al-Qaeda also used Pakistan’s tribal areas as a platform from which it could plan, direct, and support external operations against the West. These types of attacks remained important for bin Laden, who declared to his closest lieutenants, “The most important activities the [al-Qaeda] Organization can carry out are operations that directly affect the security and economy of all of the American people … . Operations inside America and targeting oil abroad … are among the strongest and fastest ways to affect the [American] people.”55
Al-Qaeda senior leaders in Pakistan also issued internal guidance and sent material support to, and otherwise interacted with, affiliated and associated groups.56 To help manage affiliates, bin Laden formulated what he referred to as his “General Policy” (al-Siyasa al-Ama), guidance that was circulated to al-Qaeda franchises and declared that al-Qaeda’s focus was the “bigger external enemy before the internal [enemy].”57 Beyond its formal affiliates, al-Qaeda leaders in Pakistan also issued advice to and otherwise engaged with the Afghan Taliban and Tehrik-e-Taliban Pakistan, among others.58
Finally, al-Qaeda’s leadership spent an extensive amount of effort in the tribal areas drafting and producing audio, video, and written statements and reports through its propaganda wing, al-Sahab. Al-Qaeda senior leaders indeed circulated guidance to members active in media production, providing instruction on appropriate content and tone.59 Al-Qaeda leaders also proofread and provided peer-review comments on each other’s statements and written products.60
By early 2004, the United States learned from captured al-Qaeda operative Hassan Ghul that scores of Arab men, including senior al-Qaeda operatives Sheikh Saeed, Abd al Hadi al Iraqi, and the eventual head of external operations Hamza al Rabia, had settled in or regularly visited Shakai, South Waziristan.61 According to Ghul, al-Qaeda leaders had established a training infrastructure in the area and were also in contact with Abu Musab al Zarqawi.62 As reported by Pakistan’s minister of interior in 2004, “Shakai had become a base for Al Qaeda, and it was used as a training and a transit camp by Al Qaeda.”63
After a Pakistani military offensive and an ill-fated peace accord, known as the Shakai Agreement, U.S. drone strikes in Pakistan’s tribal region began in June 2004, reportedly killing Pakistani militant Nek Mohammed.64 After Mohammed’s death and the dispersal of al-Qaeda beyond South Waziristan, several subsequent strikes targeted senior al-Qaeda leaders as well as militants organizing cross-border attacks into Afghanistan.65 As the United States honed its approach to collecting and synthesizing information gained from overhead surveillance, technical means, and human informants, by 2008 it also had eased operational constraints on drone strikes and eventually expanded the campaign to more regularly target militants carrying out attacks in Pakistan.66
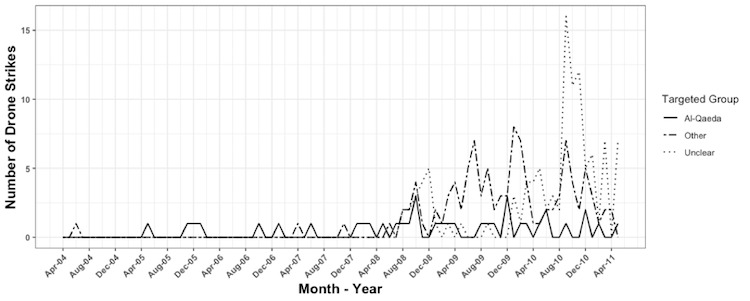
Figure 1 draws on the New America Foundation drone strike database to illustrate the increasing frequency of U.S. drone strikes in Pakistan’s tribal areas, particularly after 2007.67 As illustrated in Figure 1, the New America Foundation was unable to ascertain the target group for the plurality of strikes between 2004 and 2011. This is likely because the targets of strikes are not always apparent from media reporting, particularly in instances of near misses or where the operative is not a senior member of an organization.68
Figure 1. Monthly U.S. Drone Strikes in Pakistan, April 2004 – May 201169
Although the data may be incomplete and the affiliation of the targets are often uncertain, the trend depicted in Figure 1 can still guide the subsequent empirical analysis. As a result of the increased rate of U.S. drone strikes from 2004 to 2011, theories and claims about the campaign’s success suggest that al-Qaeda’s talent pool, organizational efficiency and control, and safe-haven viability decreased over time, while pessimistic theories and claims imply the opposite.
Personnel Quality
This section evaluates the extent to which U.S. drone strikes degraded al-Qaeda’s talent pool. If this did occur, we should expect to see succession challenges, reservations over the quality of replacements for killed operatives, and, more generally, concerns over the availability of qualified personnel. Any absence of these types of reflections or any evidence of uninhibited personnel promotions would naturally suggest that al-Qaeda’s bench of qualified operatives remained deep.
Beginning in 2005, the United States was able to successfully kill several high-ranking members of al-Qaeda. This included external operations chief Hamza al Rabia, who died in November 2005, as well as Abu Khabab al Masri, a veteran al-Qaeda explosives expert, who died in July 2008.70 Some of al-Qaeda’s military officials also were eliminated via drone strikes, including Abu Layth al Libi, a Libyan operative who had become the group’s spokesman and helped manage al-Qaeda operations in Afghanistan, as well as his deputy, Abu Sahl al Libi, both of whom died in a single strike in January 2008.71
It is apparent from the group’s internal correspondence that al-Qaeda maintained rather robust succession procedures to replace these personnel with little apprehension over the qualifications of their replacements. After Abu Layth’s demise, al-Qaeda established a clear succession plan that would eventually leave Libyan operative Abdullah Saeed in charge of the branch.72 Abu Khabab al Masri was also able to train acolytes who served as explosives instructors after his death.73 Al-Qaeda’s responses to these initial losses was thus relatively reserved: Senior leader Attiya Abd al Rahman concluded in a letter to bin Laden in March 2008 that “[w]hat has occurred in terms of the two tragedies – killing and imprisoning the mighty brothers – almost shakes the pillars.”74
There is strong evidence to suggest that this wave of drone strikes continued to erode al-Qaeda’s list of personnel who were qualified to serve in its external operations branch.
Al-Qaeda’s external operations branch is an exception. Al Rabia, himself one in a string of al-Qaeda external operations personnel who had been captured or killed after 9/11, was succeeded by Abu Ubaydah al Masri, a well-seasoned operative.75 After Abu Ubaydah died of natural causes, Abu Saleh al Somali took over the external operations section in early 2008.76 In a letter to senior al-Qaeda leaders, Abu Saleh assessed himself as being “not competent,” and further described his “limited understanding” of the branch’s strategy.77 Bin Laden would eventually concur with Abu Saleh’s sentiment and order that he be re-assigned.78
As drone strikes increased between 2008 and 2010, several senior and mid-level al-Qaeda leaders were killed. This included individuals involved in al-Qaeda’s operations in Afghanistan and Pakistan, such as Khalid al Habib and Abdullah Saeed, both of whom were tapped to oversee operations in Afghanistan after Abu Layth’s death.79 A U.S. strike also reportedly killed Osama al Kini, al-Qaeda’s chief of operations in Pakistan in January 2009.80 In addition, the list of those killed during this time period included several individuals working as officials in al-Qaeda’s external operations and in other specialist roles. Prior to the December 2009 death of Abu Saleh, the reluctant head of al-Qaeda’s external branch, drone strikes killed Rashid al Rauf and an operative named Annas, both of whom were also involved in al-Qaeda’s external operations activity.81 Mansur al Shami, an al-Qaeda ideologue and deputy to senior al-Qaeda leader Abu Yahya al Libi, was reportedly killed in early 2010, whereas Abu Jihad al Masri, a media official who had served as head of al-Qaeda’s security committee, died in an October 2008 drone strike.82
There is strong evidence to suggest that this wave of drone strikes continued to erode al-Qaeda’s list of personnel who were qualified to serve in its external operations branch. Writing in April 2009, well after the deaths of Annas and al Rauf, al-Qaeda’s external operations chief Abu Saleh complained that he lacked “required cadres” to staff a complete external operations organization.83 As mentioned above, due to Abu Saleh’s poor performance, by August 2009 bin Laden asked Attiya to find a new external operations chief. Attiya struggled to do so, however, reporting to bin Laden:
[A] real problem is confronting us now, and it is the lack of a more preferable replacement [for Abu Saleh al Somali] … after the martyrdom of the brother Rauf and brother Annas … we no longer have an appropriate individual to fill this position … . There is the brother Tufan [Adnan al Shukrijumah], but he is flawed.84
Beyond revealing the group’s shrinking personnel base, Attiya’s assessment is notable because he had previously expressed some degree of bravado regarding the extent of the group’s losses in March 2008, just around the time Abu Saleh had assumed control of the external operations branch.85
Unsurprisingly, al-Qaeda struggled to replace Abu Saleh after his death in late 2009. Sheikh Saeed offered bin Laden two options as permanent replacements. The first, Younis al Mauritani, Saeed noted, had “good, relevant knowledge, is interested in external work, and is most knowledgeable in the military sciences.”86 Saaed assessed the other, Adnan al Shukrijumah, as being competent, but noted that he had performed poorly as Abu Saleh’s deputy and was arrogant, insubordinate, and often distracted with tasks unrelated to his duties.87 Saeed eventually concluded that al Shukrijumah should oversee the branch from behind the scenes, with another individual, Abd al Rahman al Sharqi, serving as its nominal head.88 Al Shukrijumah would continue to falter, however, with both Attiya and al Zawahiri complaining that he was unable to articulate an appropriately scoped and adequately detailed “program” and remained distracted with miscellaneous tasks into the summer of 2010.89
In early 2010, shortages also became more pronounced in other areas of al-Qaeda’s personnel roster beyond external operations. In January 2010, Attiya and Abu Yahya suggested to bin Laden that rather than taking on additional responsibilities in external operations, Younis should stay in the Sharia committee. The reason they offered was that there was a “dire need for him in it [the Sharia Committee], especially after the death of Mansur al-Shami.”90
Such difficulties were not felt evenly across the organization in late 2009 and early 2010, however. A replacement security official named Abu al Wafa, whom Saeed described as “competent,” succeded Abu Jihad.91 In terms of replacing Abdullah Saeed, in December 2009 his deputy, Saidi, took over as a temporary replacement.92 Sheikh Saeed offered several options to permanently replace Abdullah Saeed, including keeping his deputy in the position.93 At the end of January 2010, Attiya and Sheikh Saeed opined that Saidi was the best choice.94 Al-Qaeda operative Uthman al Shahri assumed al Kini’s post.95 Al-Qaeda leaders would later express some reservations about al Shahri’s “diplomatic” approach, but still viewed his performance as generally strong.96
In mid-2010, drone strikes killed several more middle managers and senior leaders. The most senior operative killed was Sheikh Saeed, who died in May 2010.97 Others included Amir al Fateh, a veteran al-Qaeda military official, al Shahri, who was al-Qaeda’s chief for operations in Pakistan, as well as Abdullah al Halabi, bin Laden’s son-in-law who helped make arrangements for the movement of bin Laden’s family members.98 A string of al-Qaeda logisticians were also killed, as well as the military official Saidi, whom Attiya and Sheikh Saeed had previously recommended as a replacement for Abdullah Saeed.99
Unlike previous instances where the loss of a leader was followed by a clear proclamation from Sheikh Saeed or Attiya regarding their replacement, such discussions were absent from al-Qaeda’s correspondence after these losses. In a single letter, for example, Attiya reported the loss of 10 individuals to drone strikes, making no mention of any replacements.100 After Saidi died, Attiya simply reflected that “the middle-level leadership and cadres are tormented by the killing … compensating [for the killing] is proceeding slowly … and the spy war does not provide a large opportunity.”101 Al-Qaeda also continued to struggle to identify personnel to serve in its external operations branch. In the summer of 2010, bin Laden tasked Attiya with identifying a qualified individual to assume “general responsibility” for external work across the “regions.”102 But, by late 2010, Attiya had simply added this responsibility to his portfolio, despite viewing his existing position as already overwhelming.103
Al-Qaeda also could not identify an individual capable of overseeing an attack on U.S. soil. At the end of August 2010, Attiya discussed the possibility of tasking al-Qaeda operative al Shukrijumah with managing a “large attack inside America.”104 Both Attiya and al Zawahiri had reservations, however, due to his aforementioned poor performance in his position.105 As an alternative, Attiya proposed an operative named Abu Dujana al Basha, also with some reservation, due to his lack of experience.106 Bin Laden would respond a month later by nixing both candidates.107
Al-Qaeda’s roster of logisticians and other specialists also appeared to erode during this time. Directed by bin Laden to transport his son, Hamzah, out of Waziristan, Attiya expressed frustration with the successive loss of al-Qaeda smugglers Muhammad Khan, Mawiya, and Abdullah al Halabi, all of whom were assisting him in this matter. “Hamzah is now at our location in the region, after the death of Abd al-Latif [Abdullah al-Halabi] the projects were delayed … and the problem was compounded with the death of Muhammad Khan and the brother Mawiya a-Baluchi,” Attiya lamented. “We gave them [Mawiya and Khan] responsibility for the arrangements for the route … but shortly after returning to the region, as Allah intended, they were martyred in a bombing also.”108 Throughout the summer of 2010, Attiya also struggled to identify a suitable, available, and qualified deputy.109
There are a few exceptions to this clear evidence of al-Qaeda’s thinning bench due to drone strikes. For one, Attiya quickly assumed Sheikh Saeed’s position after his May 2010 death, and bin Laden approved his two-year term in the position in early July.110 Although prior to his death Sheikh Saeed had relayed some concerns about Attiya’s “intensity,” there is no evidence to suggest he was not qualified for the position.111 Pakistani operations chief al Shahri was also succeeded by his cousin, who, according to at least one assessment, performed better in the position.112 And, in November 2010, Attiya listed 14 individuals (three “veterans” and 10 from the “new generation”) who could be suitable for future leadership positions.113
Put simply, the evidence suggests that U.S. drone strikes outpaced al-Qaeda’s organizational processes for managing personnel turnover and mentoring new personnel.
More generally, though, toward the end of 2010 both Attiya and bin Laden reflected on the scale and detrimental effects of personnel losses. “Our situation is difficult due to a severe deficiency in cadres,” Attiya complained in November 2010.114 Bin Laden would also describe to al Zawahiri that “if the leadership dies, young leaders who do not possess all the expertise that the previous leadership did take over.”115 In a message to al-Qaeda in the Arabian Peninsula Emir Nasir al Wahayshi, Attiya also described how the “spy planes … have killed many of the leadership, cadres, and others in the past two years,” and emphasized the group’s “incomplete strength and power” in the border region.116
Based on this documented evidence, it appears that the steady increase in drone strikes degraded the quality of al-Qaeda’s personnel. In line with theories emphasizing the insulating effects of internal procedures and processes, early in the drone strike campaign al-Qaeda appeared to have had little issue replacing personnel killed by these strikes. Over time, however, this changed. First to suffer was the group’s external operations branch, which began to degrade in quality by 2008. Eventually, this spread into al-Qaeda’s branches that were responsible for local operations, as well as its logisticians. Put simply, the evidence suggests that U.S. drone strikes outpaced al-Qaeda’s organizational processes for managing personnel turnover and mentoring new personnel.
Organizational Efficiency and Control
In this section, I evaluate whether al-Qaeda’s organizational efficiency and control declined as U.S. drone strikes increased. If these components of al-Qaeda’s performance did, in fact, decrease, we should expect to see a deliberate decision by senior leaders to reduce their movement, meetings, and/or communications. This should be followed by an increase in the amount of time and resources needed to conduct routine organizational tasks, and/or an increase in apparent defections, splintering, and opportunistic behavior by subordinates.
There was a great deal of reluctance among senior al-Qaeda leaders to restrict their movement, meetings, or communications in response to drone strikes conducted between 2006 and 2008. When discussing whether the group might adjust its protocols due to U.S. strikes, Sheikh Saeed relayed to bin Laden in March 2006 that “There is an inverse relationship between the work progressing with more activity and efficiency and maintaining the execution of every security precaution.”117 Emblematic of a reluctance to reduce senior leader activity, one senior al-Qaeda leader was able to coordinate relations with the Taliban while al Zawahiri was also able to receive feedback on a draft statement from Attiya and Sheikh Saeed during this period.118 In the wpring of 2008, al-Qaeda’s leaders were comfortable meeting with a delegation from the Taliban, the emir of the Iranian militant group, Jundullah, and a journalist from al-Jazeera.119 In a historical review of al-Qaeda’s security situation in Pakistan’s tribal areas, one senior operative reflected, “I am not exaggerating in saying that we were moving around with total freedom as if we were in Kandahar at the time of the Emirate.”120
Carrying out this rather high level of operational activity, al-Qaeda leadership’s communication with affiliates appeared relatively smooth. Throughout 2006 and 2007, al-Qaeda leaders attempted to negotiate a merger between the Islamic State of Iraq and the Iraqi militant group Ansar al-Sunna, a feat that involved communicating with both parties.121 Al-Qaeda leaders were able to reach their affiliate in North Africa, al-Qaeda in the Islamic Maghreb, albeit seemingly with less frequency, but still with no acknowledged delay.122 In August 2007, al-Qaeda was also in touch with its nascent franchise in Yemen.123
Al-Qaeda’s leaders did, however, sometimes struggle to issue guidance or otherwise send personnel or other items to their affiliates, though drone strikes were not the source of these difficulties. In October 2007, for example, al Zawahiri apologized on behalf of “the brothers” for potential delays in providing al-Qaeda in the Islamic Maghreb an unspecified item or set of items, but blamed Pakistani army operations and other challenges with the route, rather than U.S. drone strikes.124 Al-Qaeda senior leaders expressed similar frustration with the “route” to Iraq and were unable to commit to sending personnel to assist the Islamic State of Iraq.125 “Perhaps the situation there [in Iraq] doesn’t necessitate committees so much as it requires following up with our brothers via communications, correspondence, guidance, and inquiries, as well as with orders,” Attiya advised bin Laden.126 In Yemen too, the ability of al-Qaeda leaders to guide the group’s affiliate seemed limited. In early spring 2008, Attiya reported to bin Laden that Yemen-based operatives had requested to launch, and then simply announced, a “branch,” leading Attiya to ask for bin Laden’s guidance.127
Through 2009, al-Qaeda’s leadership remained relatively lax in terms of its security protocols, even as strikes continued to increase. A letter written from a senior al-Qaeda leader to bin Laden in March 2009 describes a whole host of meetings among and between senior al-Qaeda leaders, their allies, and subordinates, which implies few, if any, restrictions were in place. This includes a meeting with a delegation from the Afghan Taliban, as well as the creation of a joint council comprised of members of the Tehrik-e-Taliban Pakistan and other jihadis from North Waziristan and Bajaur.128 Sheikh Saeed reported, in August 2009, that “the matters of the work are going well,” just as Attiya reported his ability to closely monitor and intervene in the external operations branch and emphasized financial and personnel shortfalls — rather than stringent operational security measures — as the key challenges facing the group.129 Although acknowledging some challenges posed by the “enemy’s strikes,” Sheikh Saeed also described an intensive leadership development course he had arranged and successfully delivered in 2009.130 And, in March 2010, Saeed described having met with and counseled al Shukrijumah several times, likely alongside other senior al-Qaeda leaders.131
Even as al-Qaeda seemed comfortable operating freely in the tribal areas, its communications with its affiliates sometimes sputtered. Throughout late 2009, al-Qaeda struggled to establish a “connection” with Iraq.132 As a result of poorly organized correspondence processes, a bevy of letters from al-Qaeda in the Islamic Maghreb composed between January and May 2009 did not reach bin Laden until September.133 Fighting in the tribal areas obstructed al-Qaeda’s ability to send an encrypted message to operatives in Somalia, and the emir of al-Qaeda in the Arabian Peninsula, al Wahayshi, would later report that, as a result of communications challenges with al-Qaeda leadership in 2009, the group “acted on our own and made some decisions” leading to a poorly managed kidnapping operation that al Wahayshi admitted “did not work well.”134
It was not until mid-2010 that drone strikes led al-Qaeda to formally restrict and decrease communication and meetings, however. In April 2010, al Zawahiri ordered a halt to meetings due to “security concerns.”135 Months later, Attiya proposed stopping much of the group’s activity in the tribal regions to avoid drone surveillance and strikes in June and July 2010.136 Bin Laden concurred, permitting Attiya to “calm things down and reduce movement to preserve your safety, as well as the safety of the supporters.”137 Prior to this, Attiya had already limited his trips to Baluchistan and had generally been avoiding traveling on highways.138
Al-Qaeda continued imposing restrictive security protocols, instructing affiliates to do so as well, from late 2010 through early 2011.139 By the fall of 2010, the fear of U.S. drone strikes led to prohibitions on Attiya and Abu Yahya’s movements, with Attiya only on exceptional occasions allowing cars that resembled local vehicles to come near his location.140 Some al-Qaeda operatives were prohibited from traveling in cars at all.141 And, in October 2010, bin Laden also gave instructions to al Zawahiri about his communication practices:
Your communications with the brothers should be through one or two brothers maximum. Do not meet with anybody else. The two brothers should be emissaries from you to the brothers and not come to you frequently, even if that leads to the delay of some of the work during this phase.142
Bin Laden would elaborate on this guidance in a similar note to Attiya.143
These measures forced al-Qaeda to exercise far greater care in performing what would otherwise have been relatively routine organizational activities, slowing its internal processes. Due to al Zawahiri’s guidance, al-Qaeda’s senior leaders did not meet in person to discuss Attiya’s promotion in the spring of 2010 and instead likely resorted to written correspondence.144 After having narrowly dodged a drone strike in early 2011, Attiya explained to bin Laden that “[even] motorcycles are getting bombed … any message and any movement is danger … . [T]he next correspondence is coming in two months … maybe three.”145 Restrictions also delayed the ability of al-Qaeda’s “coordinators” to arrange for the transfer of $1 million to the group’s coffers, as well as the release of an audio statement by bin Laden.146
Talent development and management similarly became more challenging. Attiya reflected in July 2010 that “we are working to prepare the cadres and initiate the leaders … but our circumstances are difficult, Sheikh. We are trying, but the spy war has really exhausted us.”147 Bin Laden was unable to coordinate personnel promotions with al Zawahiri likely because of the latter’s security circumstances, just as Attiya was unable to meet with a prospective deputy due to restrictions on movement.148 In early 2011, al-Qaeda operative Annas al Sabayi al Libi, apparently waiting for authorization to travel to Libya, voiced his frustration with Attiya’s delays in correspondence, writing, “He is responsible for any bad encounter that we may face along the road.”149
Although it is clear that al-Qaeda became less efficient due to its reduction in activity, the documentary evidence is mixed when it comes to whether this meaningfully affected its command and control.
By lengthening the amount of time required to consult on strategic issues, these reductions in activity may have compounded technical challenges in communications between al-Qaeda leadership and its affiliates. In March 2010, for example, al-Qaeda in the Islamic Maghreb Emir Abu Musab al Droukdal requested al-Qaeda’s direction regarding an offer of a truce from Mauritania.150 Bin Laden was still demurring on the topic in October 2010, tasking al-Qaeda’s Sharia committee to study the issue.151 Al-Qaeda in the Arabian Peninsula’s emir, al Wahayshi, similarly waited several months for strategic guidance from bin Laden regarding his activities in Yemen, receiving a summary of bin Laden’s views from Attiya in the interim.152 Attiya would eventually need to send bin Laden’s guidance to al Wahayshi via Somalia.153 The Somalia-based group al-Shabab al-Mujahideen had to wait several months for guidance from bin Laden.154 And communications with al-Qaeda’s Iraqi affiliate were scarce, if not non-existent.155
Although it is clear that al-Qaeda became less efficient due to its reduction in activity, the documentary evidence is mixed when it comes to whether this meaningfully affected its command and control. On the one hand, al-Qaeda’s leaders encountered difficulties in maintaining organizational cohesion and influence over some subordinates in 2010, just as senior leader availability declined. The behavior of a jihadi operative named Saleh al Qarawi is emblematic of these difficulties.156 Described as “trustworthy” by Sheikh Saeed in May 2007, by the summer of 2010 al Qarawi had fallen out of favor with al-Qaeda leaders due to his insubordination.157 Al Zawahiri had written to bin Laden that some of al-Qaeda’s Pakistani members wanted to defect in late 2010, and al-Qaeda senior leaders Abu Yahya and Attiya warned Tehrik-e-Taliban Pakistan Emir Hakimullah Mehsud against poaching al-Qaeda members.158 The group’s leadership further struggled to rein in the hordes of foreign fighters present in the FATA from the early summer through the early fall of 2010.159 Finally, after receiving guidance from bin Laden counseling restraint and even a potential truce with the Saleh government, al Wahayshi responded somewhat incredulously, describing to Attiya how he was “surprised by the Father Sheikh Usama’s words” and giving a laundry list of objections to his leader’s direction regarding operations in Yemen.160
There is reason to question the extent to which the increases in drone strikes and the subsequent lower profile kept by al-Qaeda’s leadership produced these effects. First, al-Qaeda’s leaders faced similar challenges in maintaining internal control prior to the added restrictions on their activities. In 2008, for example, Hamzah al Jawfi, who reportedly led a group carrying out attacks in Pakistan, was resisting al-Qaeda leaders’ direction.161 Around the same time, the group’s leadership in the Afghanistan-Pakistan border region struggled to control ambitious and opportunistic operatives.162 Al-Qaeda’s relations with some of its affiliates were also always somewhat in flux. It is thus unclear whether more expedient responses would have alleviated the interest asymmetries between al-Qaeda in the Arabian Peninsula and al-Qaeda leadership.163 A portion of the internal challenges that the group faced in 2010 also coincided with al-Qaeda’s declining funds, which may have rendered the group unable to pay some subordinates.164 This all makes it difficult to attribute these challenges solely to drone strikes.
Even if one does at least partially believe that the lower profile that al-Qaeda leaders kept in 2010 caused the defections, lack of internal discipline, and affiliate recalcitrance, the evidence still does not support the claim that reductions in movement, meetings, or communications rendered the group’s leadership entirely unable to exercise command and control. Between the spring and late fall of 2010 — a period during which operational security protocols grew more restrictive — the group’s senior leaders were still able to coordinate the activities of subordinates. In the summer of 2010, Attiya was able to meet with senior Pakistani militant Ilyas Kashmiri to pass along bin Laden’s instructions for an operation.165 Beginning in the early summer of 2010, Attiya and his subordinates were also able to successfully orchestrate the ransom exchange of an Afghan ambassador al-Qaeda had held for approximately two years.166 Al-Qaeda was also able to prepare and deploy a German operative to lead 15 militants in an attack on Bagram Airfield in May 2010.167
Most emblematic of al-Qaeda’s ability to retain control over subordinates is the operational behavior of Younis. In late winter 2010 and early spring 2011, he was able to exchange several messages with and receive instructions from bin Laden to carry out a plot targeting oil tankers. As he initiated his operation, Younis received operational support, coordination, and oversight from Attiya and Sheikh Saeed, as well as guidance from bin Laden while he and his operatives were in transit to Iran.168
Though probably frustrated by delays, affiliates also still solicited and responded to al-Qaeda leadership’s guidance. In a late 2010 note to Attiya, for example, a senior al-Qaeda in the Islamic Maghreb operative reported how the group altered the ransom demands it had already issued to France after bin Laden released an audio statement demanding that France withdraw from Afghanistan.169 In the same letter in which he resisted bin Laden’s guidance, al Wahayshi, the emir of al-Qaeda in the Arabian Peninsula, welcomed his leadership’s thoughts on using poison in an external attack.170 Al-Shabab’s behavior also aligned with al-Qaeda leadership’s preferences during this period, as the group did not announce its affiliation with al-Qaeda or declare an Islamic state.171 They also solicited al-Qaeda’s opinion on exchanging a hostage.172
The evidence regarding the relationship between U.S. drone strikes and al-Qaeda’s organizational internal efficiency and control is mixed. Lethal targeting did force al-Qaeda’s leaders to take measures that would reduce their exposure, which in turn undermined organizational efficiency. And, there is some evidence that these reductions contributed to leaders’ inability to assert control down the chain of command. Nevertheless, al-Qaeda’s leaders were far from absent or silent during this period, and instead likely remained focused on the most immediate operational priorities — what was referred to in one missive as “urgent concerns” (al-inshighalat al-ajala) — allowing the group’s control over other operational elements, such as financiers and low-level foreign fighters, to wane.173
Safe-Haven Viability
This section traces the extent to which the drone campaign led al-Qaeda to reduce its reliance on its safe haven in the FATA. The analysis centers on any changes in al-Qaeda’s willingness to absorb or train personnel, as well as to house senior leaders and their families in the region. This includes authorizations for and steps toward the diversion of incoming personnel, relocation of select operational components, and complete evacuation from the area. It also includes any assessments by al-Qaeda leaders of an increase or decrease in local support or sympathy after U.S. drone strikes.
There are numerous assessments from senior leaders that suggest al-Qaeda was comfortable in the tribal regions from 2007 through 2009.174 In October 2007, al Zawahiri wrote to the emir of al-Qaeda in the Islamic Maghreb that “the circumstances of your brothers in Afghanistan and neighboring countries is steadily improving.”175 In December 2007, bin Laden also attempted to enlist help to convince Iran to release his family members, asking a relative, “[P]lease try to facilitate their release in the Waziristan region where we can be sure of their safety among the tribes there … . [W]e want them to be released to Waziristan only.” This request reflects the senior leader’s confidence in the group’s safe haven.176
This trend continued throughout 2008 and 2009. According to one journalistic account, by 2008, “all seven of Pakistan’s tribal agencies were seen to be under the influence of Al-Qaeda-inspired militants.”177 In a March 2008 letter, Attiya reported to bin Laden, “The field here in Waziristan and Afghanistan is generally OK, Allah willing, it has positive and negative factors, but the good factors predominate and are apparent, praise be to Allah.”178 Sheikh Saeed concurred: “Regarding the security where we are, praise be to Allah, the circumstances are good,” he wrote to bin Laden in April 2008.179 In March 2009, a letter from a senior al-Qaeda leader also reflected that the “circumstances” in Pakistan’s tribal areas had gone from “good to better.”180 Accordingly, in June 2009 Attiya reported that several “mid-level” members had arrived from Iran, also noting that al-Qaeda operatives were “ready to receive” bin Laden’s family members.181 And, in September 2009, another senior al-Qaeda operative concluded that both the “field” in Waziristan and the overall “security situation” were favorable.182
In early 2010, al-Qaeda began to shift in its assessment of the FATA’s suitability to absorb incoming personnel. After a group of al-Qaeda prisoners had reached Attiya’s location, in June 2010, he expressed concerns over the safety of future released operatives “due to our security circumstances (the bombings that have exhausted us)!!”183 Bin Laden still refused to redirect all incoming personnel from the FATA, referring to new cadres as a “lifeline and replacement for those we have lost” and recommending simply shortening the orientation period for new personnel in Waziristan.184 Bin Laden seemed to apply different standards for the group’s experienced operatives arriving from Iran, though, instructing Attiya in August 2010 to keep them “in a safe place outside the bombing areas.”185
Around the same time in early to mid-2010, al-Qaeda also considered relocating operational components from the FATA.186 In January 2010, Sheikh Saeed unsuccessfully recommended that the group organize an external operations branch in Yemen, as the “field where we are [in Pakistan] is not appropriate for broad external work.”187 Similarly, in the spring of 2010 Younis wrote to bin Laden in his operational plan that “the field here [in Waziristan] has become like a trap, the killing has tormented the cadres and leaders … . [N]o step will be fruitful so long as this work is here.”188 Al-Qaeda’s leadership would later authorize the travel of Younis and his cadres to train in Iran rather than Pakistan, with Sheikh Saeed sending money with a facilitator to arrange for a suitable location and Attiya expediting Younis’ travel in the spring and fall of 2010, respectively.189
As far as how drone strikes may have affected local sympathy and support for al-Qaeda, the group never concluded that there had been an increase in support as drone strikes became more frequent.
The relocation was not limited to Younis and his acolytes. In June 2010, Attiya cited the “bombing” specifically and proposed
leaving Waziristan, at least partially but still substantially. For example, we can send some of the brothers with their families inside Pakistan like Sind, its suburbs and villages, as well as Baluchistan, and so forth … and perhaps we can send a number of the brothers from the military battalions if they arrive after the [fighting] season to their brothers in Nuristan.”190
In July 2010, a frustrated bin Laden directed Attiya “to arrange safe places far from the reach of the airplanes’ photography and bombing” for leaders and specialized cadres.191
These discussions and authorizations led to more concrete action by the fall of 2010. In response to the “bombings,” in October 2010 Attiya described how he had begun relocating operatives to Kunar and Nuristan in Afghanistan, recommending to bin Laden that al-Qaeda operatives could also be sent to “liberated” areas in Ghazni and Zabul provinces.192 Later that month bin Laden gave his subordinates some instruction on their movement: “With respect to the brothers generally in Waziristan, those who are able to hide and take the required security precautions in the region should stay in it, and with respect to those for whom hiding and taking the required precautions is difficult, the other option is for them to go to Nuristan in Kunar, Ghazni, or Zabul.”193 In November, Attiya wrote that he was complying with these orders.194 Bin Laden conveyed a similar sentiment in a December message to al Zawahiri, telling his second in command to impress upon Attiya “the necessity of expediting the evacuation of the brothers whose capabilities do not allow them to hide in the region.”195
It was not until January 2011 that bin Laden authorized the complete evacuation from the FATA. After receiving continued reports about the extent of the drone campaign, as well as annotated excerpts from Bob Woodward’s book Obama’s Wars, which described U.S. surveillance and drone strikes in Pakistan’s tribal regions, bin Laden wrote to Attiya:
It appears to me that the region has been very heavily revealed and that leaving the region completely is the best solution … [O]nce we disperse in Pakistan and Afghanistan, the enemy will lose the ability to focus the surveillance on our movements and place us under the photography and monitoring.196
Bin Laden gave similar guidance to his two sons Uthman and Muhammad, informing them that “the reason for your leaving to Peshawar is that there are general instructions for the brothers to leave Waziristan, as it is clear that the region has very much been discovered.”197
Attiya did his best to honor bin Laden’s orders and instructions. “With respect to exiting from the region, it is still delayed in terms of the men, but a number of the families have been evacuated, and other families are being evacuated now,” Attiya told bin Laden in January 2011.198 Attiya reported that some men were resisting orders to relocate, asserting that they “preferred death to being arrested.”199 Bin Laden would take issue with this sentiment, writing to Attiya less than a week before the raid on his compound, “American technology and its advanced devices cannot arrest a mujahid if he does not commit a security error.”200 Bin Laden went on to instruct Attiya to move some cadres to suburbs of Pakistani cities, provided that the security situation in Waziristan had not changed.201
As far as how drone strikes may have affected local sympathy and support for al-Qaeda, the group never concluded that there had been an increase in support as drone strikes became more frequent. This is not to say that U.S. drone strikes did not generate resentment and outrage in Pakistan. As early as 2006, for example, an estimated 10,000 Pakistanis demonstrated in Karachi to protest U.S. strikes, just as nearly 8,000 protested in the FATA.202 In early 2011, a senior tribesman in North Waziristan similarly declared, “[W]e will show to the world how to take revenge for the atrocities on our tribesmen,” after a U.S. drone strike.203
Al-Qaeda either did not observe this local outrage or was otherwise unable to channel it into material support and refuge for its cadres. Instead, both primary and secondary accounts reflect the loss of the group’s popular support in the Pakistani tribal areas as the result of U.S. drone strikes. In guidance written for affiliates, bin Laden warned against “giving the tribes more than they can handle,” telling them that “our Waziri brothers are exhausted and have said explicitly that ‘the aerial bombing has exhausted us.’”204 As one secondary account describes, “Pashtun codes of honor and protection had been eroded by aerial intimidation,” just as another mentioned that al-Qaeda militants would “bemoan the local Pashtun unwillingness to associate with militants who have become lightning rods for drone strikes.”205
The evidence presented in this section has demonstrated that drone strikes led al-Qaeda to reduce its reliance on, and eventually begin evacuating, its safe haven in the FATA. Although al-Qaeda was comfortable in the FATA through much of 2009, by 2010 it began to divert incoming personnel from the area, relocating operational components to other regions, and, eventually, dispersing. Rather than making al-Qaeda feel safer in the FATA by increasing local sympathy and assistance, drone strikes caused al-Qaeda to view locals as increasingly suspect and more hesitant to harbor the group’s operatives.
Conclusion and Implications
Debates among policymakers and scholars have yielded very different claims regarding how drone strikes might have affected the quality of al-Qaeda’s personnel, its organizational efficiency and control, and its safe haven in the FATA. This study evaluated these claims through the systematic analysis of internal correspondence between al-Qaeda’s senior leaders. This section reviews the study’s findings and examines the implications they have for policy and scholarship.
In sum, this study found that drone strikes were an effective instrument against al-Qaeda, but were perhaps not as effective nor as decisive as the most assured accounts claim. Drone strikes depleted al-Qaeda’s talent pool — particularly its external operations branch — and eventually slowed the group’s organizational processes, while steadily degrading its safe haven in the FATA. Although the temporal scope of the available archival materials only allows me to evaluate these changes up to May 2011, there is little evidence to suggest that these observed trends reversed after bin Laden’s death.206 And yet, even as drone strikes reached their peak, al-Qaeda was still able to orchestrate rather complex organizational tasks. This suggests at least a portion of its internal control remained intact even as the group faced significant operational challenges.
The significance of these findings rests on their broader applicability, as the U.S. drone campaign in Pakistan is only a single instance of a fairly ubiquitous approach to counter-terrorism. The replicability of the drone campaign’s outcome depends on whether factors that facilitated its limited success will be present in future counter-terrorism campaigns. On the one hand, al-Qaeda’s combination of bucreacratic and decentralized organizational structures and practices rendered the group difficult to succesfuly degrade.207 On the other hand, the U.S. prioritization of defeating al-Qaeda during the period examined in this study may mean that this campaign was unusually well resourced.208 Future instances of lethal targeting against less organizationally robust adversaries may thus achieve more impressive results, just as dedicating fewer resources to future campaigns could limit prospects for success.209 With this in mind, one can draw broader implications from this single case, with the caveat that future work may find that variations in these and other contextual factors render it a somewhat idiosyncratic instance of middling results.
First, this study suggests that, in the aggregate, lethal targeting can yield favorable outcomes. Nowhere in any of al-Qaeda’s documents does the group reference the counterproductive effects that many pessimistic accounts claimed the drone strikes produced. This implies that the United States, its allies, and its partners can effectively employ targeted strikes against terrorist groups as an alternative to the large-scale deployment of ground forces to clear, hold, and restore local governance to territory held by transnational terrorists or local insurgents harboring them.
Second, the still modest results of the U.S. drone campaign may mean that future campaigns of this type will imperfectly contain or limit the reach of a terrorist group, not eliminate it outright. Despite having been the target of a considerable amount of counter-terrorism pressure, al-Qaeda’s senior leaders have remained active and influential.210 U.S. policymakers should thus anticipate incomplete and even impermanent results from future campaigns and should augment lethal targeting with ancillary instruments, including bilateral and multilateral law enforcement cooperation and efforts to limit terrorist groups’ access to financial resources.
Third, the results of future targeting campaigns may be slow to emerge. U.S. drone strikes did not yield an immediate, asymmetric effect on al-Qaeda’s ability to operate. Rather, the payoff from U.S. strikes generally rose as they increased in frequency. It took years of sustained pressure for al-Qaeda to begin reflecting on many of the detrimental effects that drones were having on its organizational capabilities and processes. The required time and resources needed to produce a similar outcome could increase as terrorist groups develop and share lessons learned in countering drones or as they rely more heavily on regional affiliates.211
Renewed U.S. emphasis on interstate competition has made small-footprint approaches to countering terrorist groups more attractive. The U.S. drone campaign in Pakistan presents one viable approach, although it is one that neither quickly nor comprehensively degraded al-Qaeda. Relying heavily on lethal targeting to contain future terrorist threats will likely achieve similarly real, but imperfect, results. U.S. policymakers would do well not just to understand these limitations, but to also consider the broader range of complementary counter-terrorism instruments they have at their disposal.
Dr. Bryce Loidolt is a research fellow at the National Defense University’s Institute for National Strategic Studies in Washington, DC. The views expressed here are those of the author and are not an official policy or position of the National Defense University, the Department of Defense, or the U.S. government.